Introduction:
Hi Everyone!
Here is CS610 Computer Networks Mid Term Solved Subjective Question Answers for Sure 100% Success and Exam Preparation. All Questions are very important and repeated every time in exam.
All answers are according to CS610 Handout. Therefore all students are request to prepare these Questions for better CGPA and solid Concepts.
If any student prepare these questions answer sensibly then he no need of any other material and to prepare whole handout.
Why These Notes:
1. Time Consuming:
Mostly students are jobs holder so these are very helpful for them. As I mentioned above all are very important so you can save your time by preparing these notes in a very short time period, rather no need to prepare a complete Handout of Computer Networks CS610.All are Past Exams Questions:
Sometime students confuse about syllabus and pattern about exams questions, so these are very helpful to known about type of questions you will face in incoming exams.
3. Most Repeated:
All are from Past Exams and every time repeated. Sometime examiner change 1 or 2 words of question and its meaning remain the same. So prepare all by creating concepts.4. Completely Theoretical:
Most advantage is that all questions are Theoretical and summary of complete computer network handout. By preparing these notes you will be able to answer the any question you will face in exam.To the point Answers:
All answers given are to the point and according to university and examiner necessities. There is no additional and irrelevant material.Therefore Prepare them by creating your own concepts and write in your own words in exam. You will not forget these concepts in your future. Then you can taught to others obviously.
ALSO READ:
CS401 Assembly Language Programming
Lets Start!
The packet header incorporates objective
and source addresses.
Q 2: If 100mbps Ethernet NIC is connected to a hub which
supports 10mbps, what will be the data rate in this scenario?
This has two results. In the first
place, the center point doesn't be guaranteed to make a transmission medium.
Second, there are no crashes between traffic on 10 Mbps ports and 100 Mbps
ports.
Q 3: In connection-oriented network which type of connection
identifier is used? Support your answer with example.
ATM uses the concept of
connection-oriented networking.
Q 4: Imagine a network of 6 devices A, B, C, D, E and F. All
devices are on same packet switch. If PC A needs to send parcel to PC E, how
might bundle switch forward this bundle?
Way between
switch An and F and the complete distance went along this way
Switch A ….
switch D …. switch E
Distance =
4
Q 5: Network administrator needs audio and video service for his
network. He needs to send or get information at same information rate. Which
kind of ATM quality help detail could be applied there? Give example?
To make possible the transport of audio
and video data across Asynchronous Transfer Mode (ATM) networks, a simple, low
cost, audio/video ATM appliance, the AVATAR, has been developed. This appliance
is capable to handling uncompressed bidirectional audio and NTSC video
connections.
Q 6: We have two satellite locations, at first location one
bridge is configured and at second location 2 bridges are configured. Which
location performed will be faster? Give reason.
Satellite areas with two scaffolds
arranged will performed quicker. The brigades also provide power virtually to its
East Timor assets. An extension that has numerous ports is known as a systems
administration switch. The two scaffolds and switches are equipped for guiding
traffic to explicit organization addresses as opposed to broadcasting the
information to all gadgets on an organization fragment.
Q 7: There are two sites office A & B, both are using VPN. If
a client of another organization has any desire to send a parcel to A, then
what will be the way of behaving of organization A? How data is protected in
VPN environment?
When private network “A” wants to send a
packet to a private network “B” the packet is accepted by the VPN server. Then
a standard IP packet that has a destination address corresponding to the VPN
server at network B. The machines within network A and B don't have publicly
accessible address – Because they not on the public Internet. This is advantage
of the VPN approach.
Q 8: Star Textile has huge network of systems and switches. An
undertaking is given to IT Officer that on the off chance that some connection
goes the whole organization works without a hitch. Which routing method will be
use?
Distributed routing method is better for
this purpose because Distributed routing build the required connections with
its neighbors. Disseminated steering is more adaptable than incorporated
directing in light of the fact that every hub handles its own steering. The
result is regularly improved system performance.
Q 9: Network administrator wants to build a tunnel between sites
offices. How might he fabricate utilizing private virtual organization?
To lays out a confidential organization
that can send information safely between these two areas or organizations
through a passage. A VPN burrow interfaces the two PCs or organizations and
permits information to be sent.
Q 10: Who examine performance of network?
Performance is examined by users in the
network environment.
Q 11: How can we compute shortest path in WAN?
We utilize Djikstra's calculation to
process most brief way from every hub to each and every other hub.
Q 12: What type of switching technique is used in WAN?
WANs can use circuit-switching or
packet-switching techniques. Each change moves a whole parcel starting with one
association then onto the next. That is the reason they are called packet
switches.
Q 13: Write the names of identifiers used in ATM.
An ATM with 16-bit address, 24-bit
association identifier and association identifier incorporate. 8-bit Virtual
Path Identifier (VPI)
16-bit Virtual Circuit Identifier (VCI)
Q 14: What type of topology used in Ethernet?
Traditional Ethernet use a bus topology,
meaning that all devices or hosts on the network use the same shared
communication line.
Q 15: Difference between LAN and WAN.
In LAN (Local Area Network) network
occupies the smaller area like a room or a building. In WAN (Wide Area Network)
network occupies larger areas like cities & countries. Internet is a Wide
Area Network.
Q 16: Why fiber need for ATM?
ATM is intended to
chip away at fiber (however can be utilized with curved pair). A regular port
on an ATM switch works at OC-3 speed (155Mbps) or higher.
Q 17: Define Bridge.
A bridge is an
equipment gadget likewise used to interface two LAN portions to expand a LAN. A
typical bridge has two NICs. It just runs the code put away in its ROM.
Q 18: Ambiguity may cause the failure of any network, how parity bit check is considered in this situation.
Equality can
distinguish blunders that adjustment of odd number of pieces. We see that even
no. of bits has been changed due to noise so parity checking cannot detect this
error.
Q 19: Define default route how it is different from routing.
Routing table entries
can be twisted with a default route. If the destination does not have an
explicit routing table entry, then it uses a default route. The most common way
of sending the bundles of data is called directing. The information about
destinations is kept in routing tables.
Q 20: Defines simplex and full duplex connection?
Some association
situated advancements give full duplex while other permit on simplex
association. To communicate using a simplex connection a pair of computers must
establish two connections one from computer A to computer B and another from
computer B to A.
Q 21: How WAN capable to handle many computers?
A Wide Area Network
(WAN) is a media transmission network that covers a wide region.
Q 22: Briefly explains the working structure of thick Ethernet.
It uses thick coax
cable. AUI link (or handset or drop link) associates from NIC to handset. AUI
link conveys computerized signal from NIC to handset. The wires in AUI convey
computerized signals power and other control signals. Thick Ethernet likewise
expects eliminators to stay away from signal reflectance.
Q 23: Why ATM design chose cells over packet?
Cells are not
variable length and memory management. With cells bits can be counted as they
arrive.
Q 24: What is 10base T?
The 10Base-T standard
(likewise called Twisted Pair Ethernet) utilizes a contorted pair link with
most extreme lengths of 100 meters. This is another standard of wiring scheme. 10Base-T Ethernet is in many cases
called a star formed transport.
Q 25: What is Multicasting?
It works like
broadcasting but it does not forward frames automatically to the CPU.
Q 26: What is FDDI?
Fiber distributed
data interconnect (FDDI) is another ring innovation. Its important features
are:
It utilizes fiber
optics among stations and sends information at 100Mbps. It uses pair of fibers
to form two rings.
Q 27: Define 802.11 Wireless LAN and CSMA?
IEEE 802.11 is
standard wireless LAN that use radio signals at 2.4GHz. The more seasoned
gadgets utilize radio transmissions at 900MHz and information pace of 2Mbps. Bluetooth
determines a remote LAN for brief distances.
Q 28: Define static and dynamic routing.
Static Routing: -
Static routing is the
easiest type of directing; however, it is a manual cycle.
Dynamic Routing: -
Dynamic routing
protocols are upheld by programming applications running on the directing
gadget (the switch).
Q 29: Disadvantages of Repeaters.
Repeaters don't
perceive outline designs; they simply intensify and retransmit the electrical
sign. If a collision or error occurs in one segment, repeaters amplify and
retransmit also the error to the other segments.
Q 30: Different b/w Cells and Packets?
ATM planners picked
cells over parcels due to the accompanying reasons:
Cells are not
variable length and memory management. Handling variable length packets leads
to memory breakup. With cells bits can be counted as they arrive.
Q 31: What is the difference between the physical and logical topologies?
Physical Topology:
How the workstations
are associated with the organization through the real links that sends
information. The actual design of the organization is known as the physical
topology. It depends on the wiring scheme.
Logical Topology:
The logical topology
is the way that the data passes through the network from one device to another
without the physical interconnection of the devices. We can say that it is
characterized by the particular organization innovation.
Q 32: What is meant by Bridges STARTUP and STEADY State?
When a bridge boots
the address lists be empty (startup state). The bridge forwards frames to the
other segment if it cannot find destination address in its lists. After some time when the bridge received at least one frame from
every computer, it has the lists built (steady state).
Q 33: How can “Switched Virtual Network” are laid out?
ESTABLISHING AN SVC (switched virtual circuit):
The computer sends a
connection request to the switch attached with it. Software in the switch tracks
down an organization way to the objective and sends along the association
demand. Once the connection is established by the destination, a message is
sent back to the computer to indicate the SVC is set. If any switch or the
destination computer doesn't consent to setting up the VC, a mistake message is
sent back and the SVC isn't laid out.
Q 34: What is the concept of packet switches?
Each change moves a
whole parcel starting with one association then onto the next. That’s why they
are called packet switches. Packet switches consist of a small computer with
network interfaces.
Q 35: Write a note on Weight Graph.
Dijkstra’s algorithm
can contain weights on edges in graph. The shortest path is the path with
lowest total weight (sum of the weight with all edges). For instance, as
displayed in the figure beneath:
Q 36: Define Vector-Distance Algorithm.
Packet switches hang tight for next
update message and they emphasize through sections in message. If entry has
shortest path to destination, insert source as next step to destination and
record distance.
Q 37: What is the idea of store and forward technology?
STORE AND FORWARD: Information
conveyance starting with one PC then onto the next is achieved through store
and forward technology. In this innovation bundle switch stores approaching
parcel and furthermore forward that bundle to another switch or PC.
Q 38: How can a bridge know whether to advance casings?
The bridges organize themselves
automatically to decide which bridge will forward frames and which bridge will
not. The scaffolds speak with one another on the organization and utilize
Distributed Spanning Tree (DST) calculation to conclude which extension won't
advance edges in the event that a cycle happens.
Q 39: Compare connection oriented and connectionless Service.
In connection-oriented protocol,
authentication is needed while this is not in case of connectionless protocol.
In connection-oriented protocol, we have
to establish connection between sender and receiver while this is not in case of
connectionless protocol.
Illustration of association arranged
convention is TCP and the case of connectionless convention is UDP Internet.
TCP is an association situated
convention, it makes an association and checks whether the information is
gotten, and resends in the event that it isn't. UDP is a connectionless protocol;
it has not guarantee delivery.
Q 40: Give a comparison of wiring Schemes.
The wiring schemes are compared as
follows:
Separate handset permits PCs to be
fueled off or disengaged from network without instigating. Transceiver may be
located in an awkward place, so finely fault transceiver can be hard. In other
case, flimsy cajole link takes least of link. Disengaging one PC (on one free
association) can upset whole organization. Hub wiring merges electronics and
connections. 10Base-T is most famous on account of least expense.
Q 41: Describe permanent virtual circuits (PVC).
ATM can provide
customers with virtual circuits that look like traditional digital circuits. The
forwarding tables are automatically restored after breakdown power of
equipment. The sending table sections for such long-lasting VC's are statically
arranged.
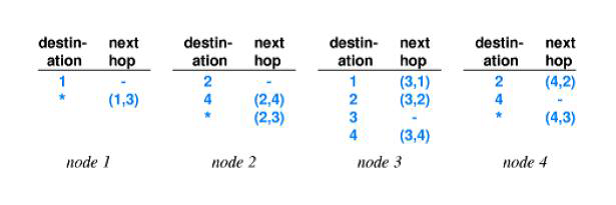
Q 42: What are default routes draw the table.
Routing table entries
can be twisted with a default route. If the destination does not have in
routing table entry, then it uses a default route. Default courses for 4 hubs
are displayed in the figure underneath.
Q 43: Star Organization use four bridges in its network and they
form a cycle. How can network engineer avoid broadcasting from all bridges in
this scenario?
If a bridge network
forms a cycle, then not all bridges on the network are allowed to forwarding broadcasting
frames. The extensions arrange themselves naturally to conclude which scaffold
will advance transmission casings and which scaffold will not. The scaffolds
speak with one another on the organization and utilize Distributed Spanning
Tree (DST) calculation to conclude which extension won't advance edges in the
event that a cycle happens.
Q 44: You are working in a star Organization as Network Engineer. The Existing Network comprises of 120 Systems. What will be your analysis about delay shout it be Smaller or higher?
The computers take turns using the medium. First one computer
uses the medium to send its data over the channel then second and so on. However,
sharing a solitary medium over significant distances is productive, because of
the long postponements. The computer with shorter delay will go first and another
computer may transmit later.
Q 45: We want to connect two site Offices, which are far away from each other. In your opinion, which one is best LAN extensions or WAN? Justify your answer.
WAN extension is best.
Reasons:
1. It integrates IT
infrastructure
2. It boosts your privacy
3. It increases bandwidth
Q 46: Suppose ABC Corporation has a small number of packet
switches and Systems. The entire works smoothly, for this type of Setup which
routing method is most appropriate? Give Reason.
STATIC ROUTING:
It is done at boot
time. It is straightforward and has low network overhead. It is inflexible.
Q 47: Explain Classification of Networks?
PC networks are gathered
by 4 fundamentals which are:
1) BY SIZE:
2) BY CONNECTIVITY:
3) BY MEDIUM:
4) BY MOBILITY:
BY SIZE:
According to their
size there are 2 organizations of networks.
1. Local Area
Network. (LAN)
2. Wide Area Network
(WAN)
BY CONNECTIVITY:
Networks are also classified
by connectivity in two topologies.
a) Point-to-Point
b) Broadcast
BY MEDIUM:
The order of
organizations is likewise founded on the Medium.
• Copper wire
• Co-axial cable
• Optical fiber
• Radio waves
BY MOBILITY:
The organizations are
likewise characterized by their mobility. In this respect there are two types
of networks.
• Fixed networks
• Mobile networks
Q 48: Define network topology and VPN?
10Base-T network
geography is a transport however wiring geography is a star. There are three
most popular topologies. • Star • Ring • Bus
STAR TOPOLOGY: In
this geography, all PCs are connected to a main issue, which is once in a while
called the "Center point"
RING TOPOLOGY: In
this topology of network the computers are connected to each other in closed
ring. In this Network first PC passes information to the second and afterward
second passes information to third, etc.,
BUS TOPOLOGY: In a
bus topology all PCs are joined to a solitary long link and any PC can send
information to some other PC.
Virtual Private
Network (VPN) joins the highlights of both private and public organizations.
Singling association and utilizations public organization for connectivity is
restricted.
Q 49: Suppose you are assigned to connect two site offices which are situated for
away from each other. One office in Lahore and other is in Paris. In your
opinion
which one will be the appropriate solution for this scenario LAN extension or WAN?
Justify your answer with reasons.
Answer:
WIDE
AREA NETWORK (WAN):
It is utilized for a
nation level systems administration and in any event, for landmasses. In WIDE
AREA NETWORK WAN, network occupies larger areas like cities &
countries.
Q 50: Suppose you want to add large number of systems in your WAN to increase its capacity. Which kind of exchanging gadgets will be utilized? Also write the names of these switching devices along with difference between them.
We can add ability to
WAN by adding more connections and bundle switches. WANs can use
circuit-switching or packet-switching techniques. Each change moves a whole
parcel starting with one association then onto the next. That is the reason
they are called bundle switches.
Q 51: Which approach of error detection is able to detect more errors as compared to others, considering that there should be no increase in the size of information being transmitted? Explain how it works.
CRC has good error detection properties. It is easy to implement
in hardware. To enable a network system to detect more error without increasing
the amount of information in each packet is called CRC.
Q 52: During data transmission, what are the possible indications if,
a) A frame is missing SOH on beneficiary side
b) A frame is missing EOT on receiver side
Missing SOH shows
getting PC missed start of message.
Missing EOT indicates
sending computer crashed.
Q 53: Network manager wants absolute privacy in his organization’s computer networks even using public network. Which innovation will be utilized and the way that it guarantees outright protection of bundles?
In addition to check packets, VPN systems use encryption to
guarantee absolute privacy.
Q 54: Suppose an organization wants to implement ATM technology in its network. Which type of connection ATM technology will provide in network?
ATM uses the concept
of connection-oriented networking. Associations in ATM are called virtual
channels (VC) or virtual circuits (a term liked by some). An ATM network is
worked from interconnected ATM switches. The connection focuses or ports can be
associated with PCs or other ATM switches.
Q 55: Suppose in computer network of a chemical company, each packet is transferred with equal amount of time between systems. Considering this scenario what will be the jitter of the network.
A network with zero
jitter takes the very same measure of time to move every bundle. An
organization with high jitter takes significantly longer to convey a few Packets.
Q 56: Write the name (Abbreviation) of ATM?
ATM stands for (ASYNCHRONOUS TRANSFER
MODE).
Q 57: How to increase the capacity of WAN?
We can add ability to WAN by adding more
connections and bundle switches.
Q 58: We have to use repeaters to extend LAN. Is there any
problem in LAN due to repeaters? Give Reason.
A bridge is an
equipment gadget likewise used to interface two LAN portions to expand a LAN. Not
at all like a repeater, a scaffold utilizes two NICs to interface two sections.
It pays attention to all traffic and perceives outline design. It also forwards
only correct complete frames and discards the crash and error frames.
Q 59: Define two types of Virtual Channel or circuit used in ATM?
VPI or Virtual Path
Indicator (8- bit),
VCI or Virtual Channel
Indicator (16-bits),
Q 60: Which of the following are Ethernet fields?
CRC, Flag, Frame Type, Preamble, Destination Address, Source
Address and Data,
Q 61: As we know when bridge network forms a cycle then not all
bridges on the network must be allowed to forward broadcast frames So tell the
which algorithm resolve this problem?
The bridges speak
with one another on the network and use Distributed Spanning Tree (DST)
algorithm to conclude which extension won't advance casings on the off chance
that a cycle happens.
Q 62: Which technology is used to copy frame data directly from main memory?
LAN interface may use DMA technology to copy frame data directly
from main memory.
Q 63: ATM network specifies a 24 bits VPI/VCI connection identifier. What number of pieces VPI and VCI possesses independently?
VPI
or Virtual Path Indicator (8- bit),
VCI or Virtual Channel
Indicator (16-bits),
Q 64: Why repeaters are not used for extension with large networks? Give at least two reasons.
Dissimilar to a
repeater, a bridge utilizes two NICs to interface two sections. It pays
attention to all traffic and perceives outline design. It also forwards only
correct complete frames and discards the crash and error frames.
Q 65: Suppose in a university campus, bridges are used in its local area network. Explain all steps, how bridge builds up address list table of all attached computers?
A bridge keeps a list
for segment that consist physical addresses of the computer attached to that
segment. In this way a bridge realizes on which fragment an objective PC is
connected. Most bridges are self-learning bridges.
When it boots its address table is empty. At the point when it
gets outlines from different PCs it fires developing its location table.
Q 66: Suppose we have to extend an Ethernet segment up to three
segments then how many repeaters will be needed for this purpose?
One repeater double,
two repeaters triple the maximum cable length limitation.
PCs joined to various
sections impart as though they are associated with a similar link.
Q 67: Assume ABC Company has two LAN segment connected through bridge. In which state both LAN segment can communicate simultaneously?
In a steady state, a
bridge allows simultaneous use of segment and then both LAN segment can
communicate simultaneously in this state.
Q 68: Is it necessary to use terminator at both ends of thin Ethernet cable? Give your answer with the solid reason.
There is a lot of signal reflectance in the network. To avoid this,
we use terminators at the end of Thin Ethernet
Q 69: A specialized computer system is used in a network in order to measure the performance of network what is specific name for such computer network and mention any three types of information it can provided in this regard?
A network analyzer
also called network monitor is used to examine the performance of a network. It
can report information such as capacity utilization, distribution of frame
size, collision rate or token circulation time.
Q 70: Define three benefits of ATM.
ATM is a solitary
innovation that is intended to meet the objectives of the two LANs and WANs. ATM
uses the idea of CON connection-oriented networking.
It transmits data at
over 100Mbps.
It utilizes fiber
optics to interface PC to switch.
Each connection
includes two fibers.
Q 71: What is the difference between LAN and WAN?
Local area network (LAN)
LAN is little in size covers the region inside a room, building
or urban communities.
Wide area network (WAN)
WAN is enormous in size and covers the region urban areas, nations and
landmasses.
Q 72: Define the term Jitter.
The term Jitter is difference
in transmission delays. Jitter is significance for
voice, video and data. Jitter can happen when a parcel is deferred on the
grounds that the network is busy.
Q 73: Briefly Explain Thick Ethernet wiring scheme.
THICK ETHERNET
WIRING:
It uses thick coax
cable. AUI link (or handset or drop link) associates from NIC to handset. AUI
link conveys computerized signal from NIC to handset. AUI link conveys
computerized signal from NIC to handset. It requires terminators to avoid
signal reflectance.
Q 74: If we have 8 computers which type of Ethernet is used thick or thin?
Thin Ethernet is helpful
when numerous PCs are found near one another.
Q 75: Give Some Advantage of bridge.
A bridge is an
equipment gadget likewise used to interface two LAN sections to expand a LAN. Most
bridges are self-learning bridges.
A bridges network can
connect many segments.
The bridges design
themselves consequently to conclude which scaffold will advance transmission
casings and which extension will not.
Q 76: Write Types of delay.
There are following
types of delay:
PROPAGATION DELAY: It defined as the time to
travel across medium.
SWITCHING DELAY: It is the time expected for
network part (hub, bridge, packet switch) to forward data.
ACCESS DELAY: It is the time expected to
oversee medium (CSMA/CD, token).
QUEUING DELAY: It is the time investigated
in packet switches.
Q 77: Suppose a network administrator wants to get automatic updates of routing information in a router, if any changes occur in the network, which routing algorithm will be used in this case? Give reason.
DYNAMIC ROUTING: It
allows automatic updates to a programmer. It can work around network
disappointments consequently.
Q 78: Routing of packet from source to destination does not depend on source address of a packet write any two advantages of this In-dependency.
It has several
benefits. It allows fast and efficient routing.
The network can keep
on working regardless of whether geography changes without advising whole network.
Q 79: Define QoS services briefly.
There are 3 kinds of
QoS determinations, which are given as follows:
CONSTANT BIT RATE (CBR):
It is utilized for
sound and video, since these have predefined greatest information rates.
VARIABLE BIT RATE (VBR):
It is utilized for
compacted sound and video where the information rate relies upon the degree of
pressure.
AVAILABLE BIT RATE (ABR):
It is used for
typical data applications (where the data rate may be unknown) and allows use
of whatever bandwidth is available at a given time.
Q 80: Which type of quality service specifies of ATM would be applied in each of the following?
(a) When network engineer want
to use ATM for compressed audio and video……CBR
(b) Network administrator needs services for typical data application…………ABR
Q 81: Suppose a network administration of XYZ
organization given a task to develop a network in a limited area with low cost
then which wiring scheme will you use? Justify your answer with reasons?
Twisted pair Ethernet is the least expensive wiring that makes it so well known.
Q 82: Describe the structure of physical address in WAN if you have (1, 5) on a switch then who will you elaborate this address?
Many WANs use hierarchical addressing for
efficiency. One part of address identifies destination switch. Other piece of
address recognizes port on switch.
Q 83: What is best in CBR VBR or ABR?
ABR (Available Bit Rate) is best, because it
is used for typical data applications and allows use of whatever bandwidth is
available at a given time.
Q 84: What service specification would be used when intend to transmit data which is less critical.
Variable Bit Rate
(VBR) And Available Bit Rate (ABR) both can be implied.
Q 85: What is the solution to avoid duplication of redundant information in address table?
Routing table entries
can be bent with a default route. If the destination is not clear in routing
table entry, then it uses a default route.
Q 86: Write down the names of switches used to add many systems to WAN. Also differentiate these switches
Interior
switch: The switch that has no
attached computers is called an interior switch.
Exterior
switch: The switch that has
PCs appended with it is called exterior switch.
Both interior and exterior switches sent packets
and they required routing tables.
Q 87: Explain how does a bridge build up its address table?
When it boots its address table is empty. At
the point when it gets outlines from different PCs it fires developing its
location table. The table is fully occupied once it had received at least one
frame from attached computer.
Q 88: Can we increase the maximum cable length as many times as we wish by just adding repeaters?
No
Q 89: Due to Which reason ATM is adopted as single underline technology.
It was designed as a
single technology for voice, video and data and has low jitter (difference in
delivery time) and high capacity.
Q 90: Which type of wireless use Wi-Fi?
See From Google or Find Its Answer yourself. Thanks











0 Comments